Oracle Identity Governance 12c has already been released. Similar to the last release it contains OIM with Identity Audit features and OPAM (Oracle Privilege Account Manager). There are some new features introduced in Identity manager part, and in this blog I will be highlighting some of them. From UI point of view, there is not major changes. End user experience will be same for access request catalog and approval/ certification.
New Configuration Features
1. OIG 12c infrastructure requires below components.
- WebLogic 12.2.1.3.0
- SOA 12.2.1.3.0
- OIG 12.1.2.3.0
- Oracle database (11.2.0.4, any 12c)
3. If you do not have DBA privilege, then you can create a script for DBA to run. Once DBA completed running the RCU generated scripts, you can run the post process configuration. This is very helpful where Database is managed by different administrative team.
4. OIM 12c finally support encryption of database. During creation of OIM users in database, RCU can encrypt database table-space. TDE (Transparent Data Encryption) option must be enabled in Oracle 12c database. TDE allow application to encrypt the table-space using secret key. Data is transparently decrypted for database users and applications that access this data. Database users and applications do not need to be aware that the data they are accessing is stored in encrypted form.
If the TDE is enabled in Oracle 12c database, RCU will automatically provide you an option to make OIM table-space encrypted.
Functional Features
1. OIM 12c introduces custom reviewer option in certification. It is applicable for Identity certification. Custom reviewer for certifications can be specified by defining certification rules in the CERT_CUSTOM_ACCESS_REVIEWERS table.
The benefit of this feature is, can now assign certification request based on a rule defined for custom reviewer.
for example
All the user who are having VISDU1 application and "EntTestDB~CN=VISD,DC=abc,DC=com" entitlement, the certifier should be "John Clark"
And
For all the other user who are having application VISDU1 but not having "EntTestDB~CN=VISD,DC=abc,DC=com" entitlement, the certifier will be the users manager.
Define the rule on CERT_CUSTOM_ACCESS_REVIEWERS table with a map name. Assign the map name in certification definition
2. OIM 12c now supports group of certifiers for Application Instance, Entitlement, Role and User certification. Till OIM 11gR2 PS3, single certifier was supported in the certification workflow.
**Group certifier assignments are not supported with CertificationProcess composite. from the configuration page CertificationOverseerProcess composite needs to be selected.
3. OIM 12c can Limit the entitlement-assignments, Role-assignment and Application-assignment to certify for each user option for creating a user certification definition. For example, while identity certification assigned to reviewer, only the selected roles, selected entitlements and selected Application instances will be visible for certification. In this way we can remove the birth rights for being certified.
5. Another new feature of OIM 12c is Inheriting the access granted via access policies from the parent role to child role. This feature is enabled by setting XL.AllowRoleHierarchicalPolicyEval system property to TRUE. For example
a) Role1 contains Policy1 which contains account A1 and entitlement E1
b) Role2 contains Policy2 which contains account A1 and entitlement E2.
c) Now Role1 is parent role of Role 2.
If XL.AllowRoleHierarchicalPolicyEval is set to TRUE, then when you grant Role2 to User1, User1 will get account A1 and entitlements E1 and E2.
If XL.AllowRoleHierarchicalPolicyEval is set to FALSE, then when you grant Role2 to User 1, User1 will get account A1 and Entitlement E2 (which are part of Role2).
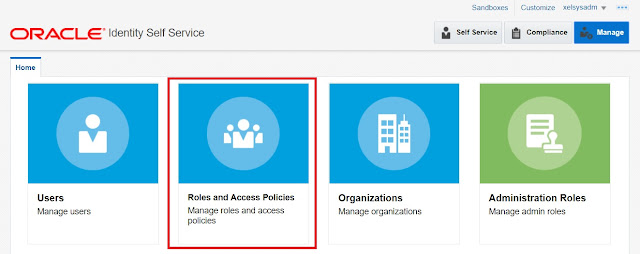
6. Access Policy can be created and managed from the Manage tab in Identity Self Service.
7. OIM 12c is now having Application Onboarding capability through GUI. It will allow you to create and manage applications, templates, and instances of applications, and clone applications. This will faster the on-boarding process of applications into OIM.
9. OIM 12c provides Real-Time Certification Purge Job capability, where old certification data can be continuously purged using this feature based on the options or choices made during configuration
10. in OIM 12c, now you can define your new connectors from all the available components. Below picture depicts the wizard, which allow you to choose components and create your new connector inside OIM.
11. OIM 12c SCIM (System for Cross-Domain Identity Management) service is now secured with custom OWSM (Oracle Web Service manager) policy. There are 2 OOTB policies oracle/multi_token_rest_service_policy and oracle/no_authentication_service_policy which enforce one of the following authentication polices when a token is sent by the client or allows anonymous when no token is supplied
- HTTP Basic
- SAML 2.0 Bearer token in HTTP header
- HTTP OAM security
- SPNEGO over HTTP security
- JWT token in HTTP header
12. OIM 12c offering JSON Web Token (JWT) service to simplify the use of Oracle Identity Governance SCIM-REST service.
The JWT produced by the OIG token service, contains a subject claim for an OIM user that is signed by the Oracle Identity Governance server. This claim can be presented for authentication to the OWSM agent that protects the SCIM and REST API.
13. Multiple sandboxes can be published in bulk and in a specified sequence using CSV file.
I will be describing in details each of the new features with live example in my next post.